External Authorisation and Balance
This documentation provides an overview of Shaype’s external balance and external authorization proposition. It outlines how the functionality works and highlights key considerations.
What is External Auth?
External authorisation is a process to enable clients to approve or reject card transactions based on their customers' balances and any other internal checks they perform. In this flow, the Shaype platform handles fraud, limits checks, account and rules, while the client is responsible for verifying their customer's balance.
To ensure accuracy in the authorisation of transactions on Shaype-managed payment channels, there must be a single source of truth for account balances, and in the external auth scenario, the account balance is held on the client’s side.
The API is designed to work in conjunction with other APIs we provide, and OpenAPI tools are available to help generate server implementations.
External Client Authorisation Flows
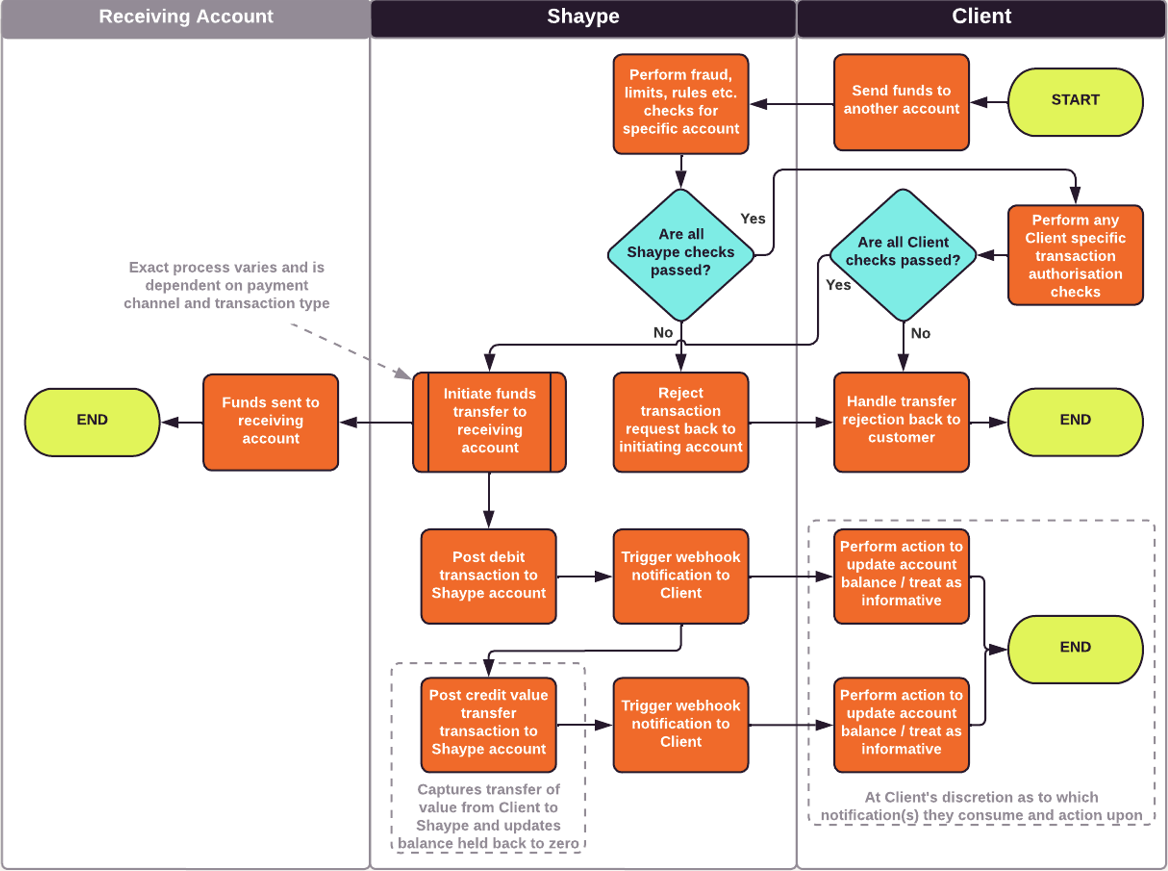
Funds Deposit
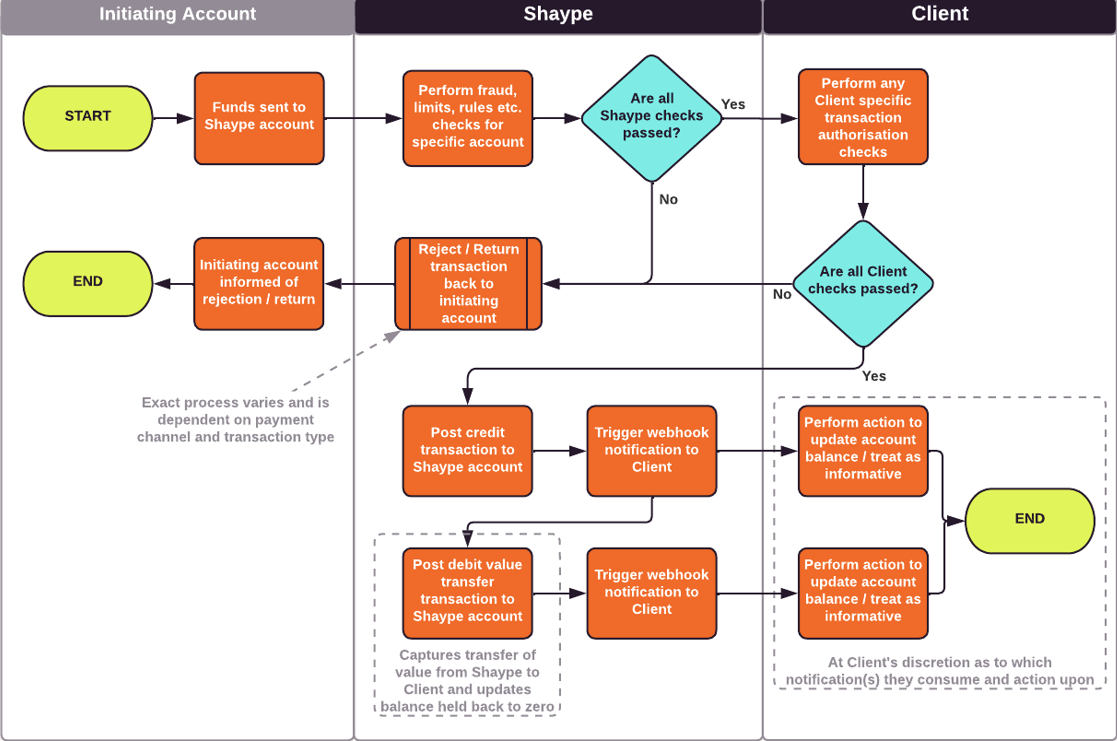
Funds Withdrawal
Platform Limit Checks
- The platform checks various limits on transactions. If any single limit is exceeded, the platform will reject the transaction without performing a balance check on the client’s side.
- The following limits are checked on transactions:
- ATM_WITHDRAWAL_PER_DAY
- TOP_UP_PER_DAY
- CARD_PAYMENTS_DAILY
- PAYMENT_TO_ACCOUNT_NUMBER
- SINGLE_CARD_TRANSACTION
- TOTAL_SPEND_PER_YEAR
APIs
Authorise a Card Hold - POST /holds
- This endpoint sends a request for the client to authorise or reject the transaction. The client can then either approve the transaction or reject it with an appropriate error code.
API Reference: Authorised a new card hold
Update a Hold Amount - PATCH /holds/{holdId}
- This endpoint would be used to increase an existing hold amount.
API Reference: Increase an existing hold amount
Authorise a Transaction - POST /transactions
- This endpoint would authorise a new transaction
API Reference: Authorise a new transaction
Response codes
Shaype requests clients to use specific response codes to indicate the outcome of hold or transaction authorizations. For a successful transaction authorisation, return a 200 OK. In the case of a failure or transaction rejection, the following outcomes must be addressed by the client with a 470 HTTP status code:
Currently, only the following two error codes are supported, any other response sent by the client will default to an outcome of INTERNAL_ERROR
- REFUSED_MAX_BALANCE_EXCEEDED
- REFUSED_NOT_ENOUGH_FUNDS
Security
Network level
HTTP-over-TLS (HTTPS) RFC2818 MUST be used for the connection.
List the IP addresses requests will be coming from. Allows the consumer to hide endpoints from the rest of the internet and avoid random scanning and probing as well as targeted attacks.
Application level
Asymmetric Key Signature. This consists of splitting a secret key into a private and public part. The private key will remain with the sender (Shaype) and will be used to sign the body of the request. The signature will be added in the headers of the request. The public key is shared with the receiver, who will use this public keys to run a verifier and check that the signature is valid.
This offers message integrity checks which a simple token doesn’t. Asymmetric keys also offers non-repudiation, it cannot be denied that it came from the sender as only they have the private key.
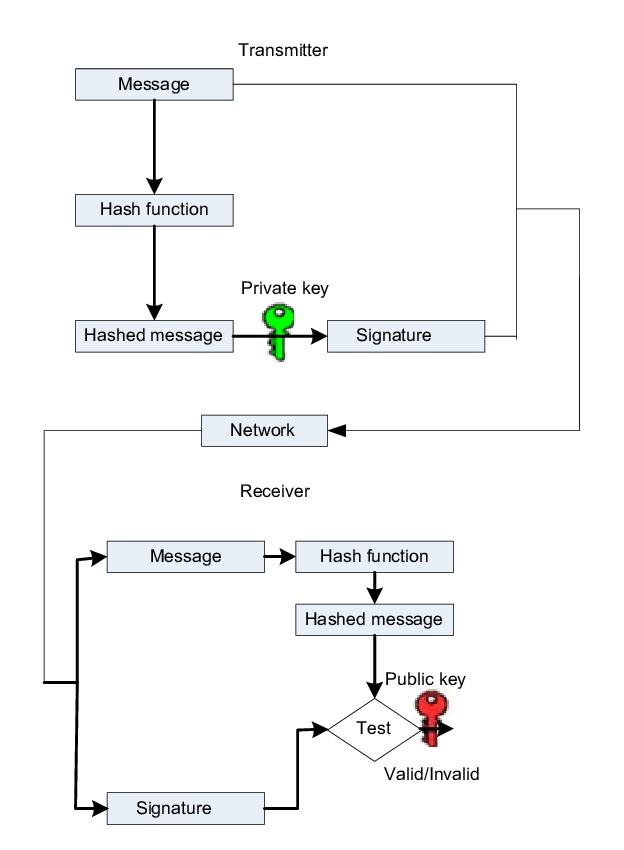
- Shaype will use SHA256WithRSA signature algorithm with 2048 bits as it offers high security and fast signature.
- A key id
Shaype-Key-Idwill be provided from Shaype in the request as a header, this can be used to retrieve the public key from our Authentication API. - The public key can be used to verify the signature in the request.
Verify Request
The process of verifying a request ensures that the payload has not been altered in transit and is securely validated.
- Capture the incoming request along with its headers and payload.
- Retrieve the public key by making a call to the
/.well-known/jwks.jsonendpoint. Filter the keys using theShaype-Key-Idheader value from the request. Store the public key in your system for future use and faster access.{ "keys": [ { "kty": "RSA", "alg": "RS256", "kid": "HCm7EWcCmpCgXFKTksFSNEx7axjn_FuutbnfKyy-69o", "use": "sig", "e": "AQAB", "n": "abcdefghijklmnopqrstuvwxyzx4885U8770YwRvf6NM3qM4kroGUhPbfqyocPs6rjtYO5BbhJQvVWOHb4XrUb8ZK-F4CfAHU4hDXEbgSoZQjAbFVBeprks5wCwKpWHsxF9K00e4HhsuqwlHEOcbZXZG5mmCNJSZNtIqoC1a1KFij7HqjHxwR7uQjlEq0jH_eDue0rdlaI9UxYE9IQxYKr1QLPkd39o4URPLNMkHbNzXy90gMEF43jIVfWBFDMQ--SrbtvHMC2HN10NeHTc2iH_6nGxzfMMDuQKpRavOsVGp_7RcWtDBRbWdkIeY9StncmK2XnA_GzCajxII7sV6-w" } ] } - Validate the signature by comparing the hashed payload against the signature using the public key. If the values match, the payload is valid and has not been altered. Below is a Java example that demonstrates how to verify the request signature.
Where,
public void verify(String signature, String publicKeyDer64, Object transactionRequest) throws NoSuchAlgorithmException, InvalidKeySpecException, InvalidKeyException, SignatureException { String requestPayload = new ObjectMapper().writeValueAsString(transactionRequest); byte[] decoded = Base64.getDecoder().decode(publicKeyDer64); // Create Public Key KeyFactory keyFactory = KeyFactory.getInstance("RSA"); X509EncodedKeySpec keySpec = new X509EncodedKeySpec(decoded); var publicKey = (RSAPublicKey) keyFactory.generatePublic(keySpec); // Verify signature Signature publicSignature = Signature.getInstance("SHA256withRSA"); publicSignature.initVerify(publicKey); publicSignature.update(requestPayload.getBytes(UTF_8)); byte[] signatureBytes = Base64.getDecoder().decode(signature); boolean verify = publicSignature.verify(signatureBytes); assertThat(verify).isTrue(); }signature: Base64-encoded signature received in the Shaype-Signature header.publicKeyDer64Public key in DER Base64 format, retrieved in step 2.transactionRequestRequest payload string (ensure it is a compact JSON string, without spaces or new lines).
Notes:
The request payload must be in string format when verifying the request signature.
Endpoint to retrieve public Keys:
Replay prevention
Each request comes with unique idempotency key. If the same request is retried it will have the same idempotency key. Idempotency key is part of the message signature. Client is advised to implement idempotent API, that means to ensure the message with the same idempotency key is processed only once.
If client is unable to implement idempotent API, then there is another option. Each request comes with the timestamp. Timestamp is part of the message signature. Timestamp allows client to define acceptable timeframe in which requests must be processed (i.e., 3-5 seconds). If request comes outside of acceptable window, then it’s ignored. For this approach to work client has to ensure server clocks are not skewed.
Notification
You will receive different notification on various transaction outcome
Transaction Type | When you will receive the notification? |
|---|---|
CARD_TRANSACTION |
|
CARD_TRANSACTION_SETTLED |
|
CARD_TRANSACTION_REFUND |
|
- In the transactionEvent object, we also have the fields accountBalances and updatedBalance, which we won’t be able to populate.
- For authorisation holds, the isPending flag is set to true, while for settled transactions, it is set to false.
Non-functional Requirements
- Requests per second (RPS) - 10
Latency:
We enforce a strict synchronous response timeout.
If a final response is not received within the applicable timeout threshold, the request will be considered failed and the transaction will be automatically rejected with outcome:
INTERNAL_ERROR
Timeout values are defined per transaction type:
- Scheme (card) transactions: 1.2 seconds (1200ms)
- Non-scheme transactions (NPP, Direct Entry, General credit/debit, etc.): 10 seconds
The timeout includes:
- Network latency (round trip)
- TLS negotiation
- Request transmission
- Client-side processing time
- Response transmission back to our platform
Round-trip latency must be accounted for within the total timeout. Our servers are hosted in London (UK). For example, for a client server hosted in Australia, round-trip network latency may reach approximately 400ms (0.4s).
Updated 9 days ago
